Wireshark Replay Pcap File
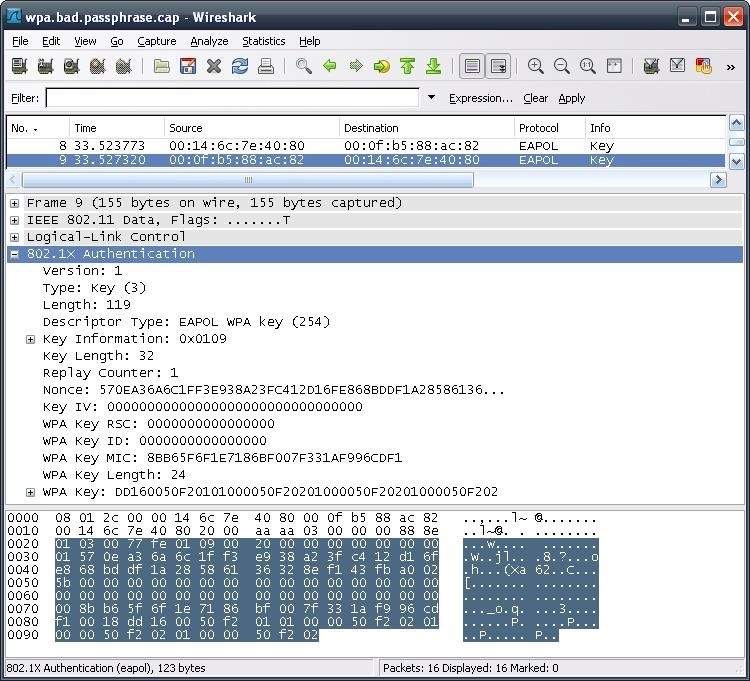
PCAP File Summary
Pcapr.net is a kind of social website to analyze and comment to traffic captures. Tshark -r file.pcap -V is very useful if you're stuck without wireshark/gui. You can simply load pcap files in Wireshark to browse them. You can directly view/capture the remote packets to wireshark using tcpdump. If you don’t provide a file extension to the filename (e.g..pcap) Wireshark will append the standard file extension for that file format. Type in the name of the file you wish to save the captured packets in, as a standard file name in your file system. Method 1 - How to import packets from a Wireshark.pcap file into STC (aka Capture Replay) Note that this method will create a stream block for each packet in the.pcap file. To create a pcap file with only the packets you want to replay see. In the case that your PCAP file doesn't open, it is highly likely that you do not have the correct software application installed on your PC to view or edit PCAP file extensions. If your PC opens the PCAP file, but it's the wrong application, you'll need to change your Windows registry file association settings. PCAP file with PowerShell Empire (TCP 8081) and SSL wrapped C2 (TCP 445) traffic from CERT.SE's technical writeup of the major fraud and hacking criminal case 'B 8322-16'. Free malware analysis sandbox. Malware samples can be uploaded or searched, PCAP files from sandbox execution can be downloaded.
Our most recent information indicates that PCAP files are associated with only a single known file type, the Packet Capture Data format, and can be viewed primarily with Wireshark, including two other known software applications (listed below). The PCAP File Extension are listed predominantly as Data Files.
The PCAP File Extension can be viewed on the Windows, Mac, and Linux operating systems. They are supported on both desktop and mobile devices. These files have a Popularity Rating of 'Low', meaning they are not very commonly observed on your average hard disk.
If you would like to learn more about PCAP files and the software that opens them, please see the additional detailed information below. Also, you can learn how to do some basic PCAP file troubleshooting if you are having trouble opening these files.
File Type Popularity
File Rank
/ 11690
What Is A Pcap File
File Status
Page Last Updated
Open your files in %%os%% with FileViewPro File Viewer
Optional Offer for FileViewPro by Solvusoft | EULA | Privacy Policy | Terms | Uninstall
Wireshark Replay Pcap File
I currently have the following, presumably standard, setup:I have a physical server with Snort running. Snort logs into its log files as it should. Those files are tracked by barnyard2 which writes the traffic to a database for Snorby.
Snort and barnyard2 are started as a systemd service. Now besides the ongoing analysis of network traffic by Snort, I want to read pcap files from a different source about every hour, applying my Snort rules to them.
Fortunately, snort provides this feature directly. However, using snort -r foo.pcap starts a new instance of Snort, which of course results in a new logfile. Barnyard2 recognizes this new log file and handles the data from the pcap as expected => the rules are fine and work for the pcap traffic. However, traffic from the Snort instance running as a service is still written into the old file and barnyard2 is not handling these packets due to the newer logfile being present.
In order to avoid this, I'm now trying to use tcpreplay to replay the pcap to my external interface, so that the Snort service can handle the packets like any other traffic. Unfortunately, Snort doesn't match on any packets if they are replayed this way. The rules working via snort -r should prove that they are correct.
Do I have to rewrite anything like MAC addresses when using tcpreplay? It may be worth mentioning that I had to recompile Snort with the --enable-non-ether-decoders parameter for it to be able to read the pcap traffic.
1 Answer
The solution was to use tcprewrite to rewrite the data link frames via tcprewrite --dlt=enet. The issue seems to be the same which required Snort to be compiled with the --enable-non-ether-decoders. I assume it originates from virtualization being involved somewhere in the observed environment.